THE LATEST FROM IP Pathways
Sharing our passion for engineering excellence and our technical expertise
The Latest From IP Pathways
Sharing our passion for engineering excellence and our technical expertise

Air Gapped and Immutable Backups Keep Data Safer from Cyberattacks
Video Transcription: A ransomware attack happens every 11 seconds by 2022, with a global cost of $20 billion yearly. Increasingly hackers are targeting data, infiltrating networks, and encrypting them during a ransomware attack. Just having a copy of data won’t keep...

9 Security Solutions Infographic
IP Pathway's Security Infographic CISCO DUO - MULTI-FACTOR AUTHENTICATION It requires a user to present a combination of two or more credentials to verify a user’s identity for login and can stop 99% of cyberattacks. SECURITY INCIDENT EVENT MANAGEMENT (SIEM) SIEM is...
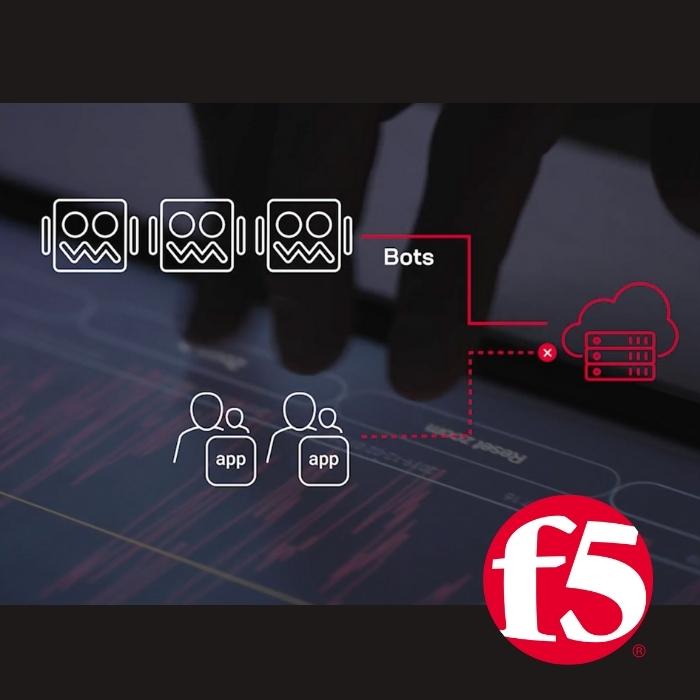
F5 Cloud Web App and API Protection (WAAP) Overview
Security and risk management leaders need to defend their businesses by protecting apps and APIs while operating at the speed of business. Friction, manual tuning, and time-consuming remediation needs to be minimized while optimizing the customer experience. As a...

Endpoint Protection (EDR) and Extended Endpoint Protection (XDR)
Endpoint protection is an effective option that must be considered when looking at your company’s overall security posture. This includes a/v and malware protection, patch management, URL filtering, and device management. Early detection and response. Your endpoint...

Cyber Insurance 101 – New Requirements in 2023
Video Transcript: Cybersecurity seems to be the # 1 concern of all the business owners and organizations we serve at IP Pathways. Security is an ever-changing landscape and cyber insurance companies' requirements are changing with it. At one time, it was enough to...

WAAP Buying Guide E-Book
What is a WAAP? Organizations that strive to deliver secure digital experiences will achieve competitive advantage by safely unleashing application innovation that delights customers. However, changing dynamics in how applications are designed and deployed have...

Cybersecurity: What You Need to Know Now
Video Transcription: The cybersecurity landscape continues to evolve. A few years ago, the only concerns were natural disasters, utility failures, and human error. Today, these threats and cyber attacks are crippling businesses and government organizations and...

Multi-factor Authentication with Cisco DUO Can Prevent Network Attacks
Cybersecurity attacks are on the rise and show no signs of slowing. Luckily, most attacks can be prevented by implementing multi-factor authentication. At IP Pathways, we use Cisco DUO for our multi-factor authentication method. While username and password login...

Everything You Should Know About API Security
We were proud to sponsor an educational program at Des Moines FutureCon in September. In this replay video, Chad Bailey, Neosec engineer, one of our cybersecurity partners, walks you through API Security. Security isn’t limited to one tool or vendor, we believe you...

Get Technology Refreshed While Preserving Capital
What is Technology on Demand? Financials can be difficult to predict and some companies, counties, healthcare institutions, and schools might have moratoriums on spending or bond issues that don’t allow additional purchases of hardware or technology services....

How to Leverage Security Tools on the Road to Zero Trust
We were proud to sponsor an educational program at Kansas City FutureCon in August. In this replay video, Michael Leggett, Solutions Architect at one of our cybersecurity partners, Avertium walks you through cloud security and zero trust and what tools are leveraged...

Managed SIEM an Important Layer in Your Cybersecurity Tool Kit
What is Managed SIEM? SIEM is an acronym that stands for Security Information and Event Management. It is a software solution that detects and monitors threats in real-time. The SIEM tools collect information and monitor all the IT assets on the network by analyzing...
